
In the era of AGI, what will we consider valuable? Likely, content that is certified as "human-made" will stand out as valuable. In other words, the focus of value evaluation will shift from the quality of the content to who created it.
Therefore, our next challenge is identifying what is human and what is not in the digital world.
Let me introduce the Humanity Protocol, which is utilizing Proof of Humanity (PoH) to create the infrastructure needed to prove our humanity and distinguish between humans and AI in the era of AGI.
“We knew the world would not be the same. A few people laughed; a few people cried. Most people were silent.”
Recalling the moment when Julius Robert Oppenheimer, the father of the atomic bomb, succeeded in developing the atomic bomb.
When OpenAI introduced ChatGPT to the world, our emotions seemed quite similar. It was hailed as the greatest innovation since the iPhone, while simultaneously sparking fears about the technology of artificial intelligence (AI). Highly advanced AI brings convenience to humanity, but that convenience can also jeopardize the survival of others. These feelings are not new. Throughout the process of inventing and mass-adopting new technologies, humans have faced existential threats as technology replaces some of the labor provided by humans.

Source: History Extra
For instance, when the spinning weaving machine first appeared, weavers felt their survival was threatened. Unable to overcome their fear of losing their jobs and being marginalized by society, they began destroying the machines that had taken their livelihoods. This protest movement is known today as the 'Luddite' movement. Interestingly, history repeats itself. With each new technological advancement, we have felt threatened. Yet, just as humanity did not become obsolete with the advent of the spinning weaving machine and continued to play a crucial role in the market post-Industrial Revolution, we will find new ways to survive.
How, then, will we live and what values will we create in the age of AGI (Artificial General Intelligence)? As I pondered this question, Marcel Duchamp came to mind. The impact of AGI on a knowledge-based society might be similar to the impact of the camera on the art world. When the camera was first introduced, many proclaimed the end of art, arguing that no painter, no matter how skilled, could compete with the camera's realistic portrayal. Yet, as we all know today, the art world is very much alive and, arguably, more vibrant than it was a hundred years ago. How did the art world adapt to the advent of the camera in such a way that it was not rendered obsolete by this new technology?

Source: Cafemontaigne
"What matters in art is not creating objects, but generating concepts.”
Marcel Duchamp
Of course, after the advent of the camera, art and painting had to change. The period following the camera's introduction can be seen as a time when the art world had to prove why what they were creating was valuable beyond just realistic representation. Marcel Duchamp redefined art with his piece 'Fountain,' introducing his own unique definition of art to the world. Duchamp's 'Fountain' is a male urinal, as seen in the photo above. Naturally, Duchamp did not create the urinal himself; all he did was sign the artist's name (using the pseudonym R. Mutt when submitting the piece) on the urinal. How could a simple, insignificant urinal change the definition of art? The answer lies in Duchamp's own words about the piece:
“They say any artist paying six dollars may exhibit. Mr. Richard Mutt sent in a fountain. Without discussion this article disappeared and was never exhibited.
What were the grounds for refusing Mr. Mutt's fountain:
Some contend it was immoral, vulgar.
Others, it was plagiarism, a plain piece of plumbing.
Now Mr. Mutt's fountain is not immoral, that is absurd, no more than a bath tub is immoral. It is a fixture that you see every day in plumbers' show windows.Whether Mr. Mutt with his own hands made the fountain or not has no importance. He CHOSE it. He took an ordinary article of life, placed it so that its useful significance disappeared under a new title and point of view – created a new thought for that object.As for plumbing, that is absurd. The only works of art America has given are her plumbing and her bridges.”
Marcel Duchamp [The Richard Mutt Case]
What Duchamp aimed to convey through 'Fountain' is simple. The value of art is not determined by universally accepted standards, but by the individual's choice and decision of what is valuable. In other words, art is not about creating within predefined guidelines but about defining and choosing what I consider to be art. Duchamp's definition successfully diluted the value given to 'realistic representation of phenomena,' which the camera could perform better than any artist. Today, we do not typically call a realistically taken photograph "art" (although, according to Duchamp's definition, if one defines it as art, it indeed becomes art).
Similarly, I believe that by extending Duchamp's approach, we can find some solutions in the age of AGI.
Many say that the era of AGI (Artificial General Intelligence) is imminent. We may soon face the threat of being replaced by AI in every field. Especially for content creators like myself, or those who create something on the internet, it often feels like AI is already superior to humans. Soon, perhaps all activities involving the use of knowledge might be replaced by AI. AI will produce better quality content, quickly access vast amounts of information, and process it into high-quality outputs. Consumers may reach a point where they can no longer distinguish between content created by AI and content created by humans. In this IT era, known as the information society, humans could become obsolete.
However, just as anything we define as art becomes art, couldn't the value in the AI era also be subjective? Even if a photograph taken by a camera is more detailed and beautiful than Duchamp's exhibited urinal, the world still regards Duchamp's urinal as more valuable. Similarly, in the AGI era, content certified as 'human-made' could be valued more highly. I believe that a time will come when who created something will be the center of value assessment, rather than the quality of the creation. As humans, this might be our only way to survive.
So, the challenge we now face is identifying what is human and what is not in the digital world. How can we distinguish between humans and AI in the digital realm? The answer to this question lies in the protocol I am introducing today. This is the Humanity Protocol, which will assign value simply by being human in the upcoming age of AI. Humanity Protocol aims to 1) enable users to prove they are human on-chain, playing a crucial role in the "human identification" I mentioned earlier, and 2) address the Sybil attack problem, which is a significant issue in the current blockchain market. Therefore, through this article, I will examine the structure of the Humanity Protocol and explain why it will play an important role in our society and, more broadly, in the digital world.
It seems evident that the Humanity Protocol will become a crucial infrastructure technology for distinguishing between human and non-human accounts in the digital world. So, how exactly does Humanity identify who is human and who is not? In this session, we will explore the structure and key concepts of the Humanity Protocol, delving into its operational principles.
The most crucial mechanism of the Humanity Protocol for identifying humans in the digital world is Proof of Humanity (PoH). PoH refers to a mechanism that verifies identity through various on-chain and off-chain processes, additionally allowing for individual identity verification. Notably, this process is structured in a decentralized manner, enabling all roles to function organically through blockchain technology and intricate tokenomics, even in environments where mutual trust is absent. The objectives that the Humanity Protocol aims to achieve through PoH are: 1) verifying that a user is human, and 2) enabling the user to self-verify as they define themselves. Let's explore the detailed aspects of the PoH mechanism below.
2.1.1 Palm Recognition
The first step in PoH is, of course, determining whether a user is human. While Humanity employs biometric verification similar to those used by traditional Web2 companies, the methodology itself is intriguingly different.
Digital identity has long been verified through biometrics, but Humanity requires a higher level of identity verification. Specifically, it involves not only a one-to-one match to confirm that a submitted biometric sample corresponds to the respective profile, but also a one-to-many match to ensure that the sample does not resemble any other profiles. This is important because, while issues like the one with iPhone's Face ID being bypassed by identical twins might be resolved now, it underscores the need for more meticulous biometric methods.
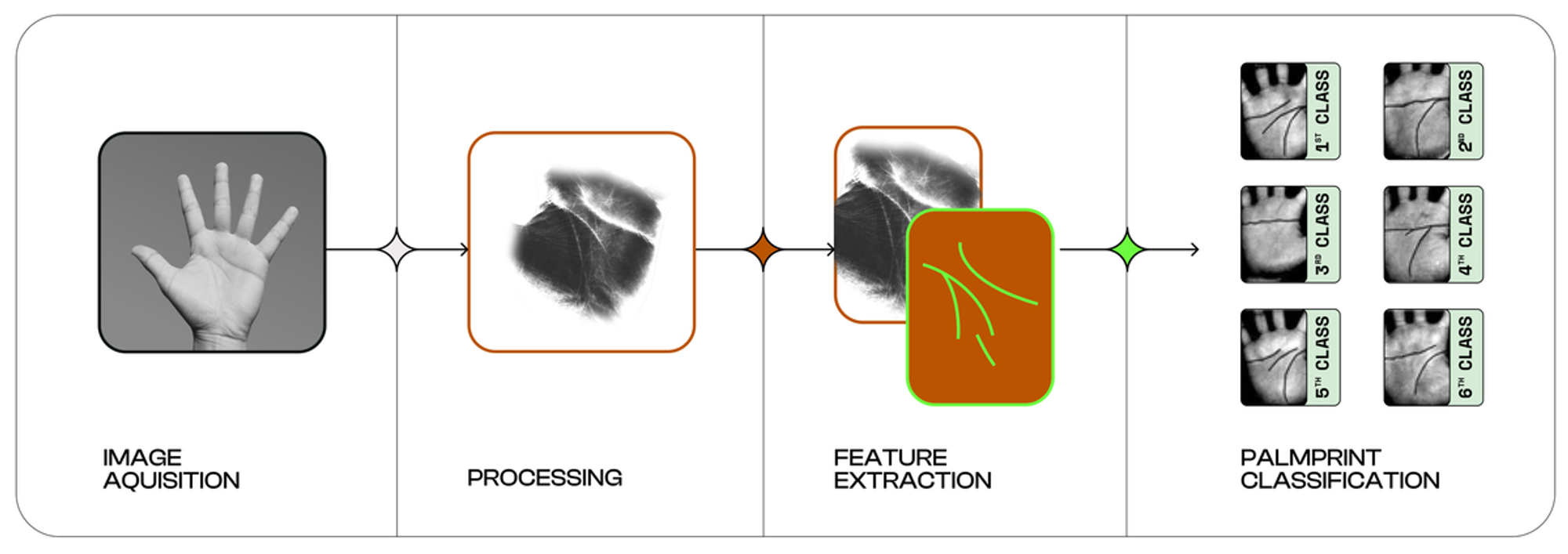
Additionally, such biometric methods may raise privacy concerns, as highly accurate biometric systems can lead to user discomfort. This is particularly true when biometric data collected is stored and managed online. For instance, collecting biometric information, including DNA data from users and their families, may meet the accuracy requirements for identity verification, but it can also make typical users uncomfortable, feeling that the technology has deeply intruded into their personal privacy. Moreover, if a third party manages the user's biometric data or holds authority over it, the potential for misuse or abuse of this data becomes a significant concern.
Therefore, Humanity uses palm recognition to verify identity while ensuring the process involves only an appropriate amount of biometric information and maximizes the protection of personal privacy.
The palm recognition module consists of two steps:
The user installs a simple program on their smartphone that recognizes a photo of their palm.
A specialized device with an infrared camera is connected to the smartphone to recognize the palm veins.
The collected and recognized images are then analyzed by the Humanity Protocol's AI model to extract unique palm features for each user. This allows for a high-verification-rate identity verification module that is accurate enough to recognize biometric information from the entire global population.
The advantages of this method are as follows:
Accuracy
Palm images have complex features unique to each individual, ensuring precise verification results. Specifically, palm vein recognition technology analyzes the characteristics of hemoglobin in the blood that interacts with infrared light, using images of the intricate vein patterns within the palm.
Reliability
The unique features of an individual's palm, including vein patterns, remain virtually unchanged throughout their lifetime. This means that users' personal profiles require minimal modification or updates.
Robustness to Spoofing
The described verification process makes it nearly impossible for malicious actors (such as AI) to spoof the system. Additional measures, like limiting the number of attempts per device, further prevent malicious activities.
Inclusivity
Capturing palm images is designed to work easily on smartphones, and while palm vein recognition requires an additional device, it is inexpensive and simple to use. Both steps are contactless.
In summary, palm recognition collects precise information while using an appropriate level of biometric data that doesn't make users uncomfortable, making it an efficient method of biometric verification.
2.1.2 Decentralized Data Storage
Data verified through palm recognition is stored in decentralized storage to ensure data sovereignty and stability. Humanity uses IPFS (InterPlanetary File System) to store user data, preventing centralized entities from misusing it.
2.1.3 Zero-Knowledge Proofs
Even though users have control over their data, if they have to share it transparently with third parties, their privacy can still be compromised. Humanity addresses this issue by using Zero-Knowledge Proofs (ZKPs), allowing users to prove they are human without revealing their data directly.
Thus, the PoH mechanism 1) securely utilizes biometric data through palm recognition, 2) stores this data in decentralized storage to ensure user data sovereignty, and 3) uses zero-knowledge proofs to verify users without exposing their data, ensuring both security and efficiency.
2.2.1 Verifiable Credential (VC)
We have explored how the PoH mechanism operates. But does this mean that the Humanity network can only be used by those who have been verified as human? Not necessarily. If a user does not pass the PoH mechanism, Humanity operates like a typical EVM-compatible Layer-2 blockchain. Therefore, in principle, anyone (human, machine, or alien) can create an anonymous wallet on the network. So, what distinguishes users who pass the PoH mechanism? The answer lies in Verifiable Credentials (VC).
VC can be seen as a unique certificate granted by Humanity. Thanks to the PoH mechanism, verified humans on the Humanity Protocol can use their wallet addresses as Digital Identifiers (DID). As Humanity evolves, a wider variety of VCs (not necessarily just for proving one is human, but also for verifying credentials such as career history, resumes, or real-world identification) can be stored in the wallet. For example:
A VC proves that the owner is a unique human within the Humanity Protocol.
VCs are more flexibly used to prove conditions such as:
Real-world identity
Education and employment history
Geographic location
Age, etc.
Examples of VCs
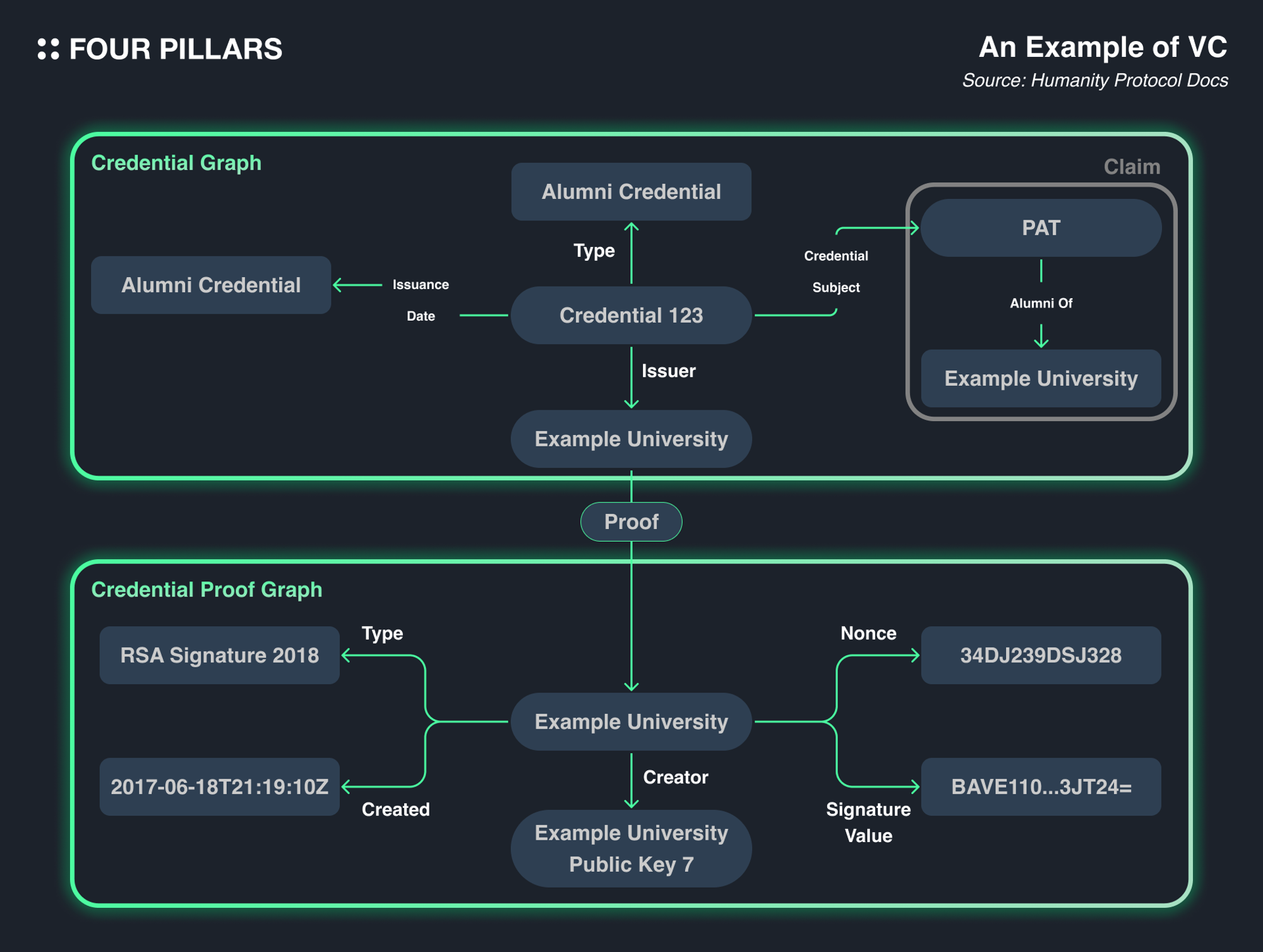
Employment History VC: A digital certificate of the user's employment history, which may include the previous employer's signature, employment period, and job title.
Educational Record VC: A digital certificate of the user's educational background, which may include the issuing institution's signature, degree awarded date, and degree name.
Age VC: A digital certificate verifying the user's age, which may include the date of birth and the signature of the issuing authority.
Based on the Humanity Self-Sovereign Identity model, human users have full control and access rights over their VCs. They can share their information directly (e.g., VCs for age and location) or indirectly (e.g., user-defined Zero-Knowledge Proofs/Verifiable Presentations (VPs)) to third parties (e.g., proving the user is over 18 and located in the EU).
Consequently, users verified as human on Humanity can perform more diverse actions and enjoy various benefits with their VCs. (Further discussion on the VCs issued through PoH and their potential uses will be provided below).
It's clear that on Humanity, users can prove their humanity with VCs and enjoy various benefits. However, a more critical question is who manages the data related to these VCs. The standout feature of Humanity lies in its methodology for managing certificates (VCs) issued through PoH. If these certificates were managed by a centralized entity, it wouldn't be much different from existing identity verification systems. The traditional Web 2.0 identity verification mechanisms have significant privacy issues due to centralized data collection and processing, which are not user-centric. Additionally, centralized systems lack interoperability across platforms, making them less suitable for the characteristics of Web 3.0. Therefore, simply using blockchain technology while maintaining this centralized concept would be highly inappropriate. This is why the current identity verification mechanisms within Web 3.0 are so inadequate.

In centralized identity mechanisms, each application exclusively manages the database of user identities and personal data. As a result, users need to manage various identities and credentials for logging in to different applications, making unified access across platforms extremely difficult. Consequently, users must repeatedly perform these tasks for each app.
On the other hand, federated identity mechanisms involve multiple applications forming a "federation" that mutually agrees to share user identities and login credentials (e.g., using a Google account to log in to a new website). While federated identity mechanisms improve platform accessibility compared to centralized systems, both centralized and federated models feature issuing authorities with exclusive control over user data, which poses a significant risk.
How should this be addressed in Web 3.0? A common misconception is that Web 3.0, being permissionless and allowing data exchange without trust, negates the need for clear identities. However, a permissionless environment still requires verified identities to give blockchain and Web 3.0 greater significance. Nevertheless, this doesn't mean that identity-related data in Web 3.0 should be managed by a centralized third party, as it would undermine the core values of Web 3.0.
What if identity-related data in Web 3.0 could be managed by the individuals themselves? Humanity addresses this by implementing the concept of Self-Sovereign Identity (SSI).

Before diving into how the SSI framework operates, let's take a closer look at the key roles within it. There are three primary roles in the SSI framework: the user (Holder), the Identity Validator (Issuer), and the zkProofer (Verifier). When a user needs a VC, the Identity Validator issues it, and when the user wants to use the VC, the zkProofer verifies its validity and whether the user can use it.
To help readers understand, imagine that the user, Identity Validator, and zkProofer correspond to the police department issuing a driver's license, the holder of the driver's license, and the police officer checking the driver's license and its holder for accuracy, respectively. When a driver's license is used as an ID, the person checking the ID acts as the zkProofer. The police department is responsible for verifying the applicant's identity and issuing the driver's license, ensuring the document's credibility. The issued driver's license is then presented to a police officer or third party for verification to confirm its authenticity and match with the holder.
Similarly, the Identity Validator, zkProofer, and user work together organically within PoH to ensure smooth operation, motivated by the Humanity Protocol's tokenomics, discussed later. Before that, let's examine these roles in more detail.
2.3.1 Identity Validators
Identity Validators verify personal data submitted by users and issue VCs if the data is valid. For example, an educational institution can issue a VC regarding a user's graduation status but has no access to the user's driver's license status. The Humanity Protocol supports more complex Verifiable Presentations (VPs) that include both non-personally identifiable information and personally identifiable information VCs. Creating these complex VPs requires collaboration between the Humanity Protocol core platform and Identity Validators. Because Identity Validators are ultimately responsible for the authenticity of issued VCs or VPs, they are considered trusted entities like sequencers in rollups. (Since VP is another form of VC, it will be referred to as VC unless specified otherwise.)
While anyone can theoretically become a verifier and issuer in a fully decentralized environment, this is not desirable for Humanity, which deals with potentially sensitive personal data. Therefore, Humanity plans to develop the protocol in two stages, balancing decentralization with data security:
In the first stage, the focus is on creating an environment where Identity Validators can issue VCs without issues. This involves Identity Validators processing palm data collected from the identity verification module and issuing VCs only when the user is verified as human and the palm data does not overlap with other users' data. This stage also includes generating zero-knowledge proof VCs (VPs) used for external applications.
In the second stage, entities wanting to become Identity Validators will be granted authority through $HP token staking. These authorized Identity Validators will function as certified entities with the right to verify users' KYC data, similar to authorized financial institutions. Identity Validators will have fixed terms determined through governance processes, including candidate nominations and network-wide elections.
Here’s how Identity Validators perform their roles:
Assume a user has requested a VC.
The user's VC metadata is uploaded to the user's dedicated storage space on the IPFS decentralized storage system.
The user grants access and shares the decryption key with two randomly selected Identity Validators for 2 hours (access to the decryption key expires after this time limit).
Within this time frame, Identity Validators independently verify the user's identity off-chain and express the result as [Yes | No | Uncertain]. The verification summary includes:
The user is a real person (or entity).
The personal data is valid.
The personal data originates from the user.
If the consensus is "Yes," Identity Validators update the encrypted database, issue the VC and zero-knowledge proof, and propagate the updated account status across the network.
If Identity Validators reach different conclusions, three additional Identity Validators participate in the verification process. The majority opinion determines the issuance outcome, and those in the minority have a portion of their staked $HP slashed as a penalty.
2.3.2 Humanity zkProofers
zkProofers play a crucial role in receiving, processing, and verifying various VCs or VPs. They verify and process VCs when users interact with third-party dApps. Thus, zkProofers operate with strict sensitivity and rigor regarding personal data management. Unlike Identity Validators, zkProofers do not need to hold $HP stakes but require a separate license to operate. To prevent centralization, multiple zkProofers are necessary, and the network incentivizes diverse zkProofer participation.
We have discussed the essential roles of Identity Validators and zkProofers in the SSI framework. The key takeaway is that for Humanity to function ideally, appropriate incentives must be allocated to these roles. So, how does Humanity provide these incentives?
The tokenomics of the Humanity Protocol aims to provide appropriate motivation for each role to ensure PoH operates smoothly and to impose penalties when necessary, creating a fair and sustainable system. Emphasizing decentralization, the tokenomics implements a system of rewards and penalties.
2.4.1 $HP
The token, which is the most fundamental requirement for the composition of the Humanity Protocol's tokenomics, carries the ticker $HP. Within the Humanity Protocol, the primary uses of $HP are as follows: 1) payment of fees when using the Humanity Protocol, 2) rewards for Identity Validators and zkProofers, and 3) as a governance token for decision-making processes.
Transaction Fees: Users will pay fees in $HP when utilizing the Humanity Protocol.
Rewards: $HP will be given as rewards to Identity Validators and zkProofers for their contributions to the ecosystem.
Governance: $HP will serve as a governance token, allowing holders to participate in decision-making processes within the protocol.
2.4.2 How those participants got incentivized?
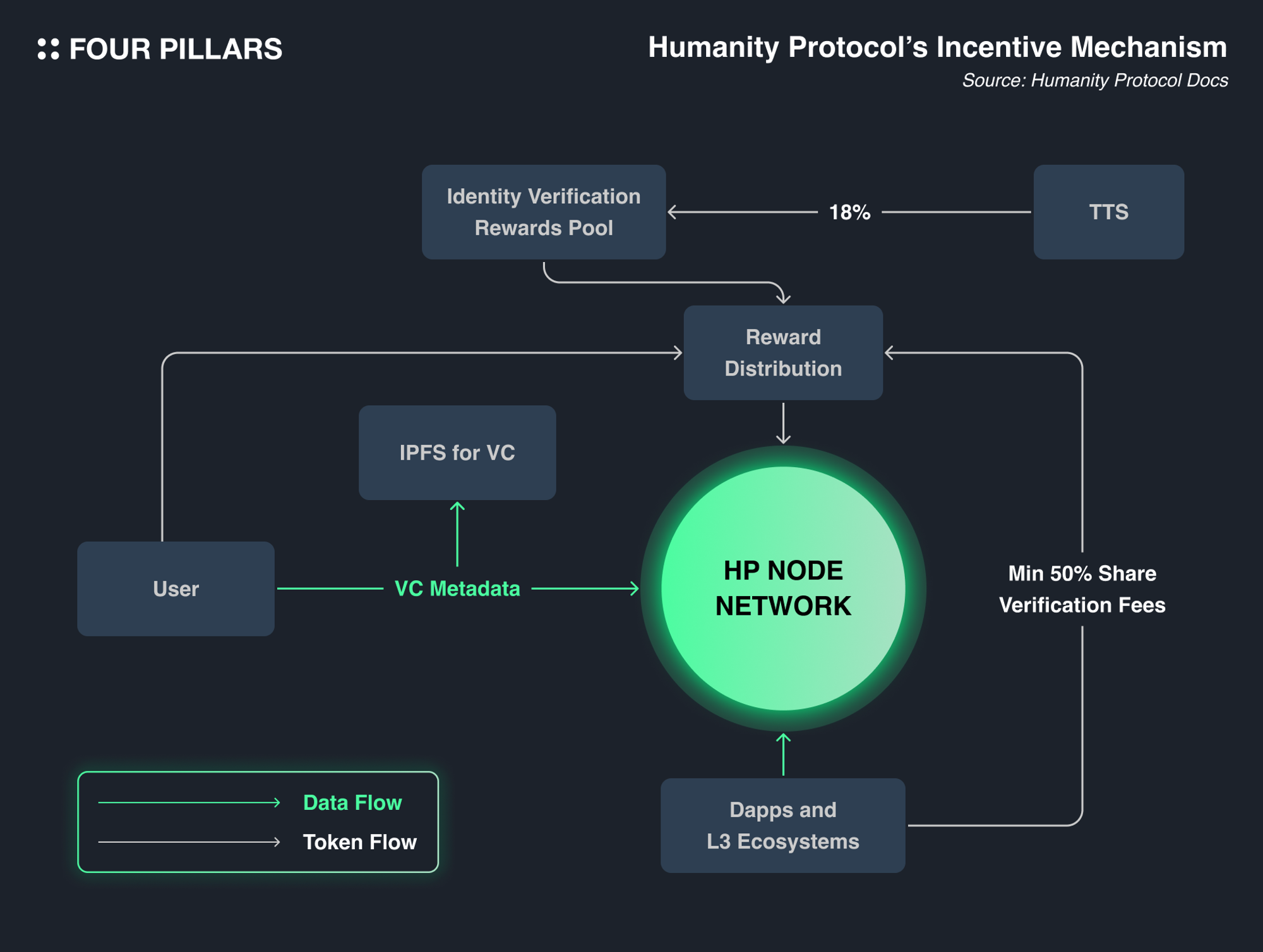
For each role within the Humanity Protocol to receive rewards, they must diligently perform their respective tasks and contribute positively to the ecosystem. Adequate compensation is provided to motivate these roles, ensuring the Humanity Protocol operates seamlessly through its tokenomics.
Firstly, users are not the primary recipients of rewards in this tokenomics structure. While the Humanity Protocol may offer $HP tokens for marketing purposes, users primarily act as consumers of $HP, paying fees to conveniently verify their identity through the Humanity Protocol and use it across various dApps.
Secondly, Identity Validators, who must be trusted entities, are required to stake a significant amount of $HP to operate. Therefore, the Humanity Protocol provides staking rewards for this staked $HP, fostering a cooperative relationship within the tokenomics framework.
Lastly, zkProofers are compensated for verifying the content of VCs and VPs and facilitating interactions between users and dApps. Their rewards come from a pool of $HP allocated for identity verification rewards and at least 50% of the verification fees paid by users and dApps. To attract more participants to the zkProofer role, the Humanity Protocol has introduced three different categories: Basic, OG, and Founder. Each category has a distinct reward structure to ensure smooth operation. Allocation to these categories is determined through a fair lottery system.

As mentioned earlier, the Humanity Protocol is not an EVM blockchain network restricted to verified humans. Instead, it is a blockchain network that achieves optimal performance when identities are verified and appropriately utilized. Let's explore some potential use cases for the Humanity Protocol.
A basic income exclusively for humans may seem less effective in a world where non-human entities are on the verge of digital entry. However, as the digital world evolves, the number of entities whose humanity is uncertain will increase, enhancing the value of assets reserved for humans. Addressing both the impending influx of non-human entities and the issue of duplicate claims due to sybil attacks, a UBI system implemented with the Humanity Protocol can achieve fair wealth distribution by ensuring that only verified humans receive benefits.
A common issue in current Web 3.0 airdrop events is that a single participant can create multiple wallets or accounts, making near-infinite attempts to participate in the event. With the Humanity Protocol, identity verification includes duplicate prevention, ensuring that each participant can only make one attempt. This 1:1 match between the physical and digital worlds simplifies the resolution of sybil issues and extends to fairdrop events.
Social networks are widely recognized as communication channels between humans. The key point is that these are channels between humans. When unverified entities participate, anonymity and lack of accountability can lead to unforeseen issues, such as spreading false information or committing fraud. While such issues exist currently, increased anonymity and irresponsibility could exacerbate them. To prevent this, a social network composed exclusively of verified humans is necessary, which can be achieved using the Humanity Protocol.
With the advent of blockchain technology and the rise of DAOs, the concept of a digital nation has become a recurring topic. A social network, as described previously, forms the foundation of this digital nation if rules, laws, and governance systems are established. The critical component, however, remains that humans must be at the center. Voting, a crucial aspect at the national level, must be transparent and fair, adhering to the principle of one person, one vote, and avoiding sybil issues. Utilizing the Humanity Protocol's objectives can lay the groundwork for such a digital nation.
As initially illustrated with Duchamp's example, Humanity is expected to create a new value system by distinguishing between human and non-human entities. In the human-centric network states discussed in section 3.4, humans will establish standards and laws, with the primary value centered on "being human." This could lead to a new value system where content (whether art, videos, or written works) is valued for being created by humans, preserving the worth of human-created works. Unlike the productivity revolution of the Industrial Revolution, this would be a "humanity revolution."

With the rise of AI and the emphasis on human identity, many projects in the Web3.0 industry are focusing on this area, including the Humanity Protocol. One project that preceded the Humanity Protocol in this regard is Worldcoin. Like the Humanity Protocol, Worldcoin focuses on verifying human identity but aims for economic equality by distributing Worldcoin. Despite the different end goals, both projects share common ground in utilizing identity verification. Let's delve into the differences between these two projects.
The Humanity Protocol revolves around Proof of Humanity (PoH), while Worldcoin uses Proof of Personhood (PoP). Although the terms have subtle differences in meaning and nuance, each has unique characteristics in their internal components.
4.1.1 Palm Recognition vs. Orb
There is a difference in the methods of identity verification. The Humanity Protocol uses palm and vein recognition, whereas Worldcoin employs iris recognition. Iris recognition boasts a high accuracy rate due to the unique patterns in a person’s iris but requires high-resolution cameras and specific infrastructure, making it difficult to use in certain environments. In contrast, palm and vein recognition is less known and has a lower adoption rate, but it also offers high accuracy, is cheaper and easier to set up, and can be used in any environment where palm information can be captured.
The palm recognition hardware of the Humanity Protocol is set to be released in two forms. One is a device similar to a POS system that can scan palms for commercial use, and the other is a simple dongle-type hardware for personal use. Due to its simplicity, verification is easy, and it offers excellent scalability. Those who possess this hardware can act as a hub by scanning others whom they trust, allowing them to participate in the Proof of Humanity (PoH) process and receive rewards.
4.1.2 Verifiable Credential vs. World ID
Verified users receive a form of certification in both PoH and PoP. In the Humanity Protocol, this is known as a Verifiable Credential (VC), while in Worldcoin, it is referred to as a World ID. Both VCs and World IDs focus on identity verification and ensure that users’ personal data is protected under strict privacy systems. However, their use cases differ: the Humanity Protocol aims for integration with various platforms, while Worldcoin focuses on distributing basic income globally.
4.1.3 $HP vs. WLD
Both $HP and WLD tokens have their own tokenomics. They share the common goal of rewarding users who verify identities and contribute to the ecosystem. Both tokens also serve as utility tokens that can be used in governance. However, the Humanity Protocol’s rewards are directed towards roles that contribute to the ecosystem's growth, whereas Worldcoin distributes tokens as a form of universal basic income to all users.
The Humanity Protocol has clear goals and various systemic features to ensure stability and efficiency. While it offers distinct features compared to similar projects like Worldcoin, it is not without its potential issues. This chapter explores the potential problems and the solutions Humanity Protocol has in place.
The Humanity Protocol aims to address one of the key issues, which is ultimately privacy. Personal information is essential for identity verification and preventing Sybil attacks, but if the management of this personal information is inadequate, it can result in harm to the users. To resolve the issues related to this double-edged sword of personal information, the Humanity Protocol employs a method that manages user data and VCs in a decentralized manner and uses them securely.
VCs issued by trusted institutions within the Humanity Protocol are linked to users’ wallets, with user data maintained in an encrypted state. The encryption keys are split and stored across distributed nodes, ensuring decentralized key management and eliminating central dependency. This allows users full ownership and control over their keys.
All encrypted user data is stored in decentralized off-chain storage systems, such as IPFS. This ensures redundancy and data retrieval while preventing duplication. IPFS assigns addresses based on the content stored rather than conventional domain or IP addresses.
Storing and managing personal data is important, but using this data securely is equally critical. The Humanity Protocol categorizes personal information into two types for use.
For non-personally identifiable information and state information verification, users directly share their data with verifiers. The VC itself, issued by a trusted institution, provides high reliability.
For other cases, users and verifiers use a trusted third party for indirect information sharing. This method employs Verifiable Presentations (VPs), allowing users to selectively share only the necessary information. VPs enable users to combine or extract specific parts of their VCs, preventing unnecessary data exposure and protecting personal privacy more effectively.

Source: Netflix
In October 2015, AlphaGo shocked the world by defeating one of the top Go players, Lee Sedol. Many people proclaimed, "Professional Go is over," believing that no human could ever again outmatch AI in Go. Yet, nine years later, numerous professional Go players continue to compete fiercely on the international stage (International Go Federation, China, Korea, Japan).
Why is this? Humans fundamentally enjoy competing against other humans, not against entities that surpass human capabilities. The value of any endeavor lies in human competition. This is evident in sports: there are many things that can run faster than humans, yet we place value on human speed. As long as humans are the ones assigning value, we will continue to create new value systems and persevere in our own unique ways.
We inherently fear AGI, not only because it might control our lives, but more so because it might replace us. However, I believe the era of AGI presents an opportunity to reconsider what it means to be human. What has been taken for granted—our very humanity—might become our most crucial value system. Although there is much discussion about the integration of blockchain and AI, I see the primary importance of blockchain in the AGI era as providing the infrastructure for humans to prove their humanity. Everything else is secondary. While we must wait to see how Humanity will function once it launches its mainnet, the reason to maintain keen interest in this project is clear.
The rise of AGI underscores the need for humans to reaffirm their unique identity. Despite our fears, this technological evolution challenges us to re-evaluate and cherish what it means to be human. Blockchain offers the means to authenticate our human identity, making it an essential component in this new age. Observing Humanity’s progress will be crucial as it may very well define how we assert our place in a rapidly evolving digital world.
We produce in-depth blockchain research articles

Starting with a social wallet using Web2 social logins, Particle Network now focuses on simplifying multi-chain complexities with their core product, Universal Account Stack (Universal Account, Liquidity, and Gas). In this article, let’s look into the core components when crypto users interact with and what exactly Particle Network is building to provide the “Future of Crypto UX.”

This is a piece explaining the problems defined by the KYVE Network and the unique structure of the KYVE Network.

In the trading phase of crypto adoption, where most crypto assets are concentrated, exchanges need an infrastructure that is both highly reliable and does not compromise the trading experience. A hybrid exchange design approach, like that of Cube.Exchange, can be suitable in this regard.

It discusses how The Graph can play a crucial role in creating synergy between AI and blockchain.